The Russian Trail in the Latest 'Ransomware' Attack
The Russian Trail in the Latest 'Ransomware' Attack
The developers of the exPetr virus didn't want ransom: Their goal was to attack Ukrainian interests.
Photographer: Vincent Mundy/Bloomberg
It's almost a reflex to blame Russians for cyberattacks
these days, even on the sketchiest of evidence. But such accusations
certainly seem justified regarding the novel ransomware attack that has
swept the world in recent days -- known as notPetya, exPetr, Petrwrap
and several other names referring to its similarity to the well-known
Petya ransomware.
On April 28, Ukrainian President Petro Poroshenko introduced sanctions against a number of Russian companies, including the hugely popular social network Vkontakte and the near-indispensable accounting software developer 1C. The latter was a huge blow to Ukrainian accountants, especially those working for small and medium-sized businesses. 1C, built from scratch by Russian Boris Nuraliev, who is now a billionaire, is established throughout the former Soviet Union because it has made a point of understanding and integrating the vagaries of each country's accounting rules while keeping its software basic, reliable and easy to use for someone without any information technology competence. It also worked as a cheap alternative to sophisticated enterprise resource planning software like that from German vendor SAP.
Ukrainian business publications filled with articles on "how to replace 1C," used by some 300,000 local firms. Many of these mentioned M.E. Doc -- a Ukrainian software package that had the advantage of being one of two programs authorized by the Ukrainian tax service for the filing of electronic returns. It's with the M.E. Doc software that the exPetr virus attack originated, according to Microsoft (whose software's vulnerability the virus exploited), Ukrainian cyberpolice and the cybersecurity company Kaspersky. The malware was apparently embedded in an automatic update to the accounting package.
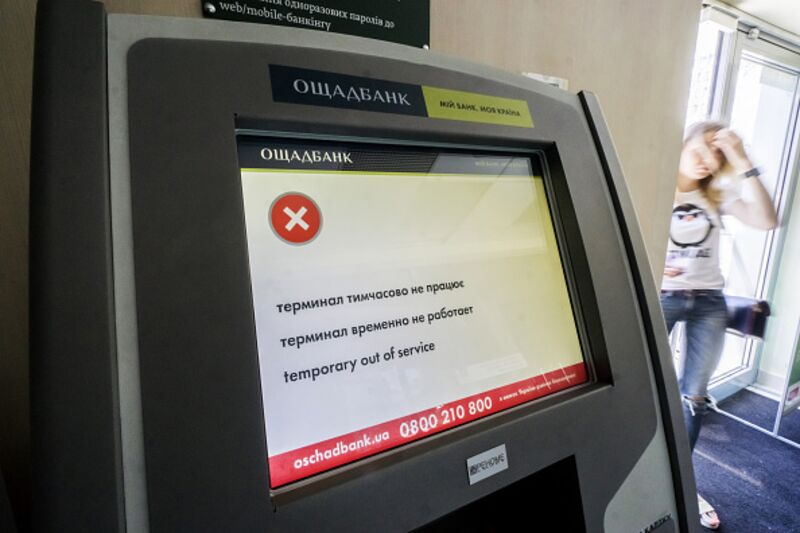
That's why the infection spread disproportionately in Ukraine, hitting airports, railroads, large banks, mobile operators, energy companies, government offices, even the decommissioned Chernobyl nuclear plant, where technicians monitoring it had to switch to manual radiation control.
The malware rebooted computers and displayed a red screen telling the victims to pay $300 in Bitcoin to have all their files decrypted. It transpired soon that the malware's developers didn't really want the money. There was a single email address specified for contact with the hackers, but it was soon blocked by the service provider, as usually happens in these cases. Besides, it turned out that the virus encrypted the victims' hard disks without the possibility of recovery. That's odd: An attacker who wanted money would have taken care he could receive it, or at least would have demonstrated his ability to decrypt the files.
So cui bono; who benefits from this? Ukrainian officials were quick to accuse Russia of waging cyberwarfare against their country -- but that's almost white noise these days, coming from Kiev, and many observers were confused by the malware's seeming geographic indifference. It hit large Russian companies, too -- the state-oil giant Rosneft and the giant steelmaker Evraz, among others.
That, however, was likely collateral damage. Evraz owns a large Ukrainian coking coal producer. Rosneft sold most of its Ukrainian assets last year, but a map on its website shows it still has an operation in Ukraine. The global shipping firm Maersk, one of the biggest victims of the attack, has a Ukrainian presence, too. It has posted a job listing for an economist with M.E. Doc skills.
On Wednesday, Vesti, the news program on Russian state television, reported that "the virus had such a field day in Ukraine because of the ban on Russia's 1C." Other Russian propaganda outlets carried this version, too.
It would fit the snarky style of President Vladimir Putin's Kremlin to launch such a mocking attack on Ukraine using a vulnerability that had long been exploited by the U.S. National Security Agency, until it was stolen and published by a hacker collective calling itself Shadow Brokers. Proof will be hard to come by, but even Russian cybersecurity experts don't see what happened as an ordinary ransomware attack.
"This is a test of a certain digital weapon, a training exercise of a cyberarmy with concealed attribution," Ilya Sachkov, head of Group-IB, one of Russia's biggest cybersecurity companies, told Hacker magazine, while admitting he had no specific proof. "The goal would be how much damage could be inflicted on business and how people would react."
On Wednesday, North Atlantic Treaty Organization Secretary General Jens Stoltenberg said NATO
had decided a cyberattack could trigger Article 5 of the treaty, which
calls on member states to come to the defense of a country that's being
attacked. That, however, is an empty threat until countries learn to
attribute attacks like the exPetr one with more certainty, and until
common capabilities are in place to analyze and defeat such threats. In
this particular case, as in some others around the world, circumstantial
evidence points to Russian involvement, and the private cybersecurity
community is happy to discuss it, but governments -- even the Ukrainian one, long aware of the cyberthreat across the border -- have proved helpless and slow to react.
On April 28, Ukrainian President Petro Poroshenko introduced sanctions against a number of Russian companies, including the hugely popular social network Vkontakte and the near-indispensable accounting software developer 1C. The latter was a huge blow to Ukrainian accountants, especially those working for small and medium-sized businesses. 1C, built from scratch by Russian Boris Nuraliev, who is now a billionaire, is established throughout the former Soviet Union because it has made a point of understanding and integrating the vagaries of each country's accounting rules while keeping its software basic, reliable and easy to use for someone without any information technology competence. It also worked as a cheap alternative to sophisticated enterprise resource planning software like that from German vendor SAP.
Ukrainian business publications filled with articles on "how to replace 1C," used by some 300,000 local firms. Many of these mentioned M.E. Doc -- a Ukrainian software package that had the advantage of being one of two programs authorized by the Ukrainian tax service for the filing of electronic returns. It's with the M.E. Doc software that the exPetr virus attack originated, according to Microsoft (whose software's vulnerability the virus exploited), Ukrainian cyberpolice and the cybersecurity company Kaspersky. The malware was apparently embedded in an automatic update to the accounting package.
That's why the infection spread disproportionately in Ukraine, hitting airports, railroads, large banks, mobile operators, energy companies, government offices, even the decommissioned Chernobyl nuclear plant, where technicians monitoring it had to switch to manual radiation control.
The malware rebooted computers and displayed a red screen telling the victims to pay $300 in Bitcoin to have all their files decrypted. It transpired soon that the malware's developers didn't really want the money. There was a single email address specified for contact with the hackers, but it was soon blocked by the service provider, as usually happens in these cases. Besides, it turned out that the virus encrypted the victims' hard disks without the possibility of recovery. That's odd: An attacker who wanted money would have taken care he could receive it, or at least would have demonstrated his ability to decrypt the files.
So cui bono; who benefits from this? Ukrainian officials were quick to accuse Russia of waging cyberwarfare against their country -- but that's almost white noise these days, coming from Kiev, and many observers were confused by the malware's seeming geographic indifference. It hit large Russian companies, too -- the state-oil giant Rosneft and the giant steelmaker Evraz, among others.
That, however, was likely collateral damage. Evraz owns a large Ukrainian coking coal producer. Rosneft sold most of its Ukrainian assets last year, but a map on its website shows it still has an operation in Ukraine. The global shipping firm Maersk, one of the biggest victims of the attack, has a Ukrainian presence, too. It has posted a job listing for an economist with M.E. Doc skills.
On Wednesday, Vesti, the news program on Russian state television, reported that "the virus had such a field day in Ukraine because of the ban on Russia's 1C." Other Russian propaganda outlets carried this version, too.
It would fit the snarky style of President Vladimir Putin's Kremlin to launch such a mocking attack on Ukraine using a vulnerability that had long been exploited by the U.S. National Security Agency, until it was stolen and published by a hacker collective calling itself Shadow Brokers. Proof will be hard to come by, but even Russian cybersecurity experts don't see what happened as an ordinary ransomware attack.
"This is a test of a certain digital weapon, a training exercise of a cyberarmy with concealed attribution," Ilya Sachkov, head of Group-IB, one of Russia's biggest cybersecurity companies, told Hacker magazine, while admitting he had no specific proof. "The goal would be how much damage could be inflicted on business and how people would react."

No comments